My role
Created strategic concept mockups and collaborated with UX researchers to clarify user requirements through interviews and get internal alignment from PMs and directors
Consolidated cross-platform design solutions to align with PM’s business direction and technical team’s roadmap
Team
1 Product Manager
2 Program Managers
2 Architects
2 Threat Experts
4 Software Engineers
2 Frontend Engineers
1 UX Research
3 UX Designers
1 Visual Designer
2 Technical Writers
Am I at risk of the latest cyber threat campaign?
The problem was frequently asked by our customers when the industry started whispering a suspicious cyber threat activity was discovered.
When a cyber threat occurs in the field, a security operation manager would ask whether the environment is affected. Moreover, a threat hunter needs to hunt for indicators to prevent a potential outbreak. While Trend Vision One platform has the technology to detect different attack indicators in all security solutions, the platform lacks the association of the attack indicators and a consolidated view from the threat event perspective.
The MVP release to test the water
To tackle the problem, in early 2022, I worked with threat researchers, architects and PM to sort out the threat intelligence data Trend Micro has. The initial goal was to release informational reports to highlight the noticeable details of the indicators of a threat event. It was identified as the threat intelligence hub in the platform and the data can support the correlations of threat detections in the future. Within the granularity of a cyber threat, the Threat Actor, known as the attacker group, is the most recognised by the field in general. We associated the indicators of the threat with threat actor reports as the first release.
The initial report content did not catch much attention since only a few user environment-related threat association was shown in the report. The feedback received from the in-site survey showed that the lack of association with their security condition lost their interest. On the other hand, it was a good indicator that the users do need threat intelligence data. Thus, PM initiated the strategy discussion within the team to plan for the future phases.
Planned Threat Intelligence UX strategy from three aspects
The three types of threat intelligence services in cyber security.
There are three types of threat intelligence usage in a security team. Following the MVP release, the next goal was to propose the experience and value to get other PMs and directors on board. After PM’s business direction sharing, I conducted stakeholder interviews to learn from the UX researcher and threat researcher to understand the three aspects and the technical feasibility. The concept demo went well, and the key stakeholders agreed to proceed.
The strategic threat intelligence concept mockups I proposed to PMs and directors.
Parked the Strategic Threat Intelligence After Interviews
To start with, by the end of 2022, PM formed an assumption that strategic threat intelligence is the most efficient way to sell its value. The hypothesis is that during the past year, the security product buying centre has shifted from the IT team to the Security Operation Centre (SOC). That is, the SOC manager is the key person with the budget.
To validate the idea, the UX researcher interviewed the selective high-engaged customers’ SOC managers to learn how threat intelligence data benefits their security task planning. The result went out surprisingly: except that one of our lead customers is mature enough to interpret the strategic threat intelligence data, other customers in the interview have less intention to consider this as one of the factors in resource planning. As SOC managers, they care more about the actual attack and the strong indicators in the environment.
The result was unexpected but was a great insight to us. We parked the strategic threat intelligence planning and moved forward to the comparably growing markets: tactical and operational threat intelligence. Tactical threat intelligence was covered in another project, so the following will focus on tactical threat intelligence.
Evolved the Operational Threat Intelligence: The Threat Hunting Story
Following the threat technology team’s roadmap, in mid-2023, I initiated the discussion of tailoring the operational threat intelligence, the threat hunting story, on the Trend Vision One platform. My role at this stage was to clarify the use cases and details with the threat technical team, PMs, and developers and design high-level user flows.
Threat hunting is to look into threats proactively and is considered an advanced threat investigation skill. The target user of the operational threat intelligence is threat hunter and advanced security analyst. The user profiles are difficult to recruit. Considering our in-house threat researchers are advanced threat hunters, the UX researcher and I worked closely with them to learn about their hunting methods.
The following are the key takeaways that are critical to threat hunting:
To hunt for a potential threat, a user needs an indicator of attack (IoA) as the search criteria. A precise IoA can filter out neutral cyber detections in the user’s environment to get more solid proof
Vendor guidance showing the product capability helps to prevent or remediate the threat
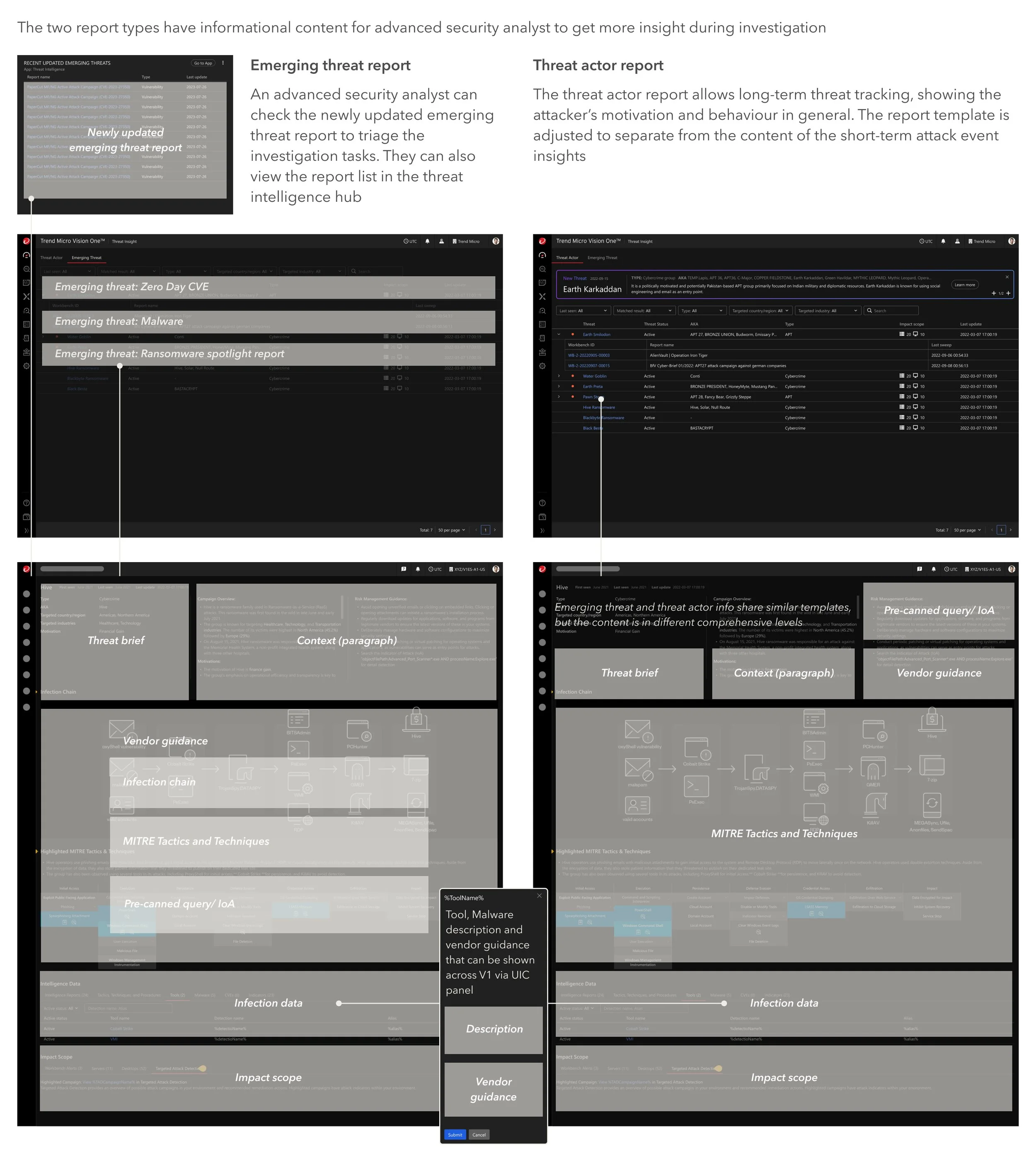
A threat actor report does not reflect the threat information in its emerging phase
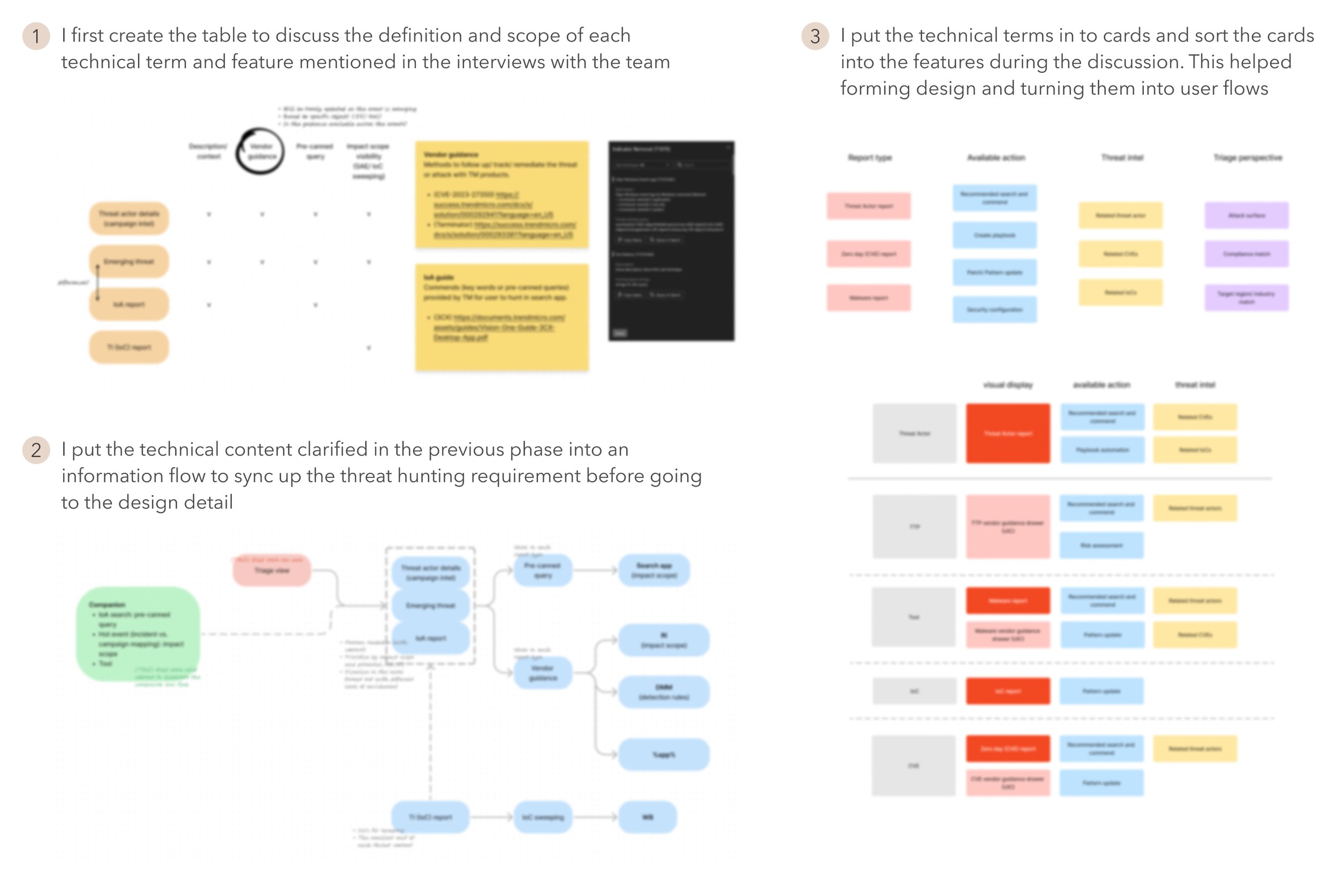
With the information we got, I arranged a few meetings to conduct informal open card-sorting sessions to get the alignment of the definition of each technical term and its feature feasibility. Combining the user requirements learnt from the threat researchers and the existing security solutions, we proposed two end-to-end flows of threat hunting on the Trend Vision One platform.
The informal card sorting and design methods I used to align the user requirements and technical capabilities with the team.
Use case I: Advanced security analyst hunting with the emerging threat reports
An advanced security analyst may have threat knowledge but need more guidance to form the hypothesis to investigate proactively. As the existing threat report is aimed at the threat actor information, we created the emerging threat report type to provide more insights. In the emerging threat report, we consolidated the IoAs and intelligence data of the attack in a certain period. A user can search the matched data in their environment with one click. With the newly updated security pattern as vendor guidance, an emerging threat report has a more practical use of threat hunt. Moreover, to help prioritise the hunting focus, we created a widget in the security dashboard, sorting the emerging threat reports by their last active time.
The discussion materials helped clarifying the design details after we got the alignment from the open card-sorting.
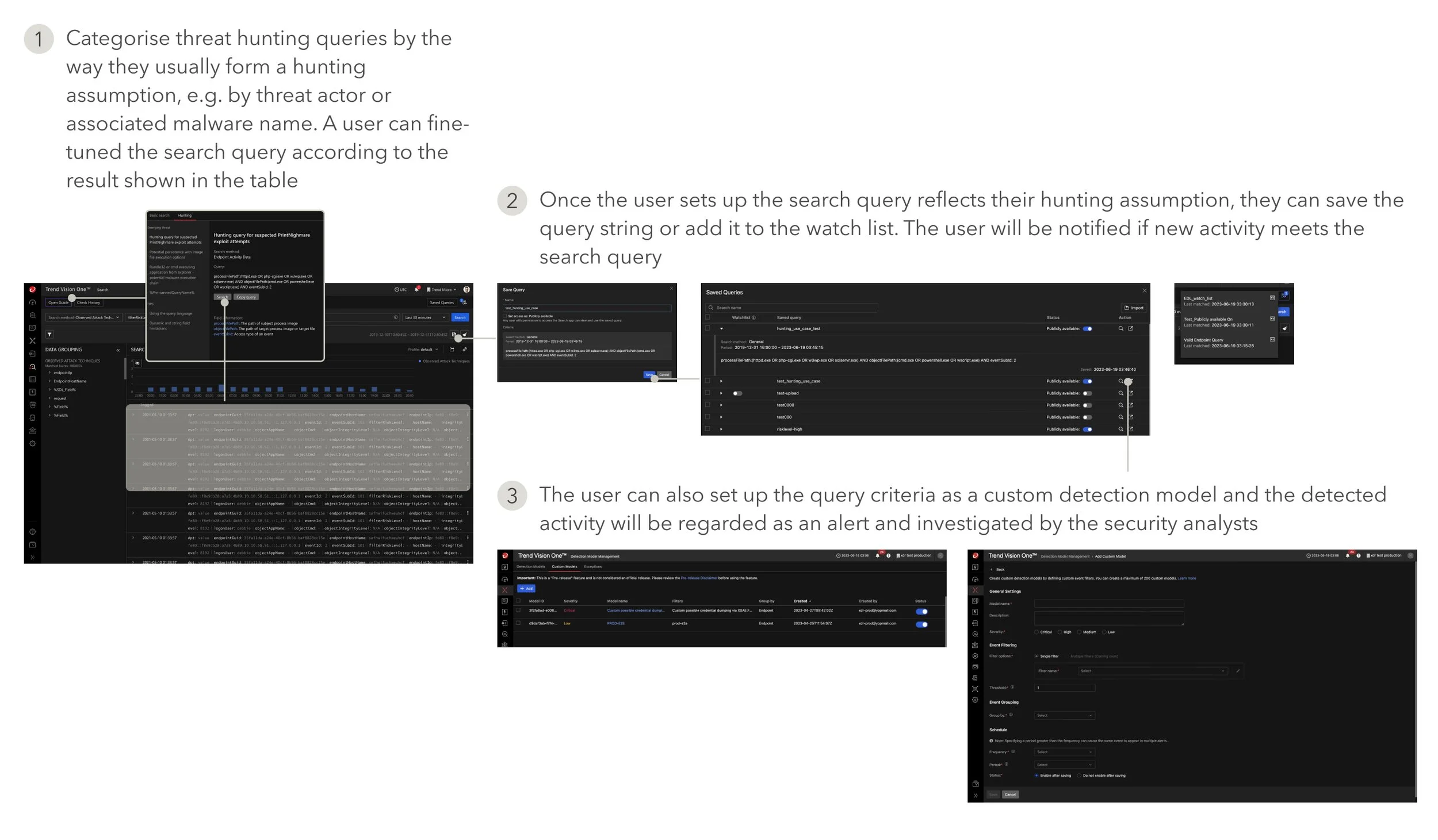
Use case II: Threat hunter hunting from raw logs
A threat hunter, on the other hand, has a stronger sense of identifying suspicious activity occurring in the environment. They form hunting hypotheses from experience and can iterate the hypothesis and fine-tune the IoA criteria through the hunting process. A well-categorised IoA list and the details of the IoA query criteria are enough for them to elaborate, thus, threat intelligence data itself becomes the hunting reference. A user’s act should start from a raw log search, where the search result can reflect the query's preciseness. They can determine whether to broaden the investigation scope with the associated threat intelligence data shown aside, such as the emerging threats using the same attack tactic. I proposed to tailor the design with other existing features on the platform to complete the threat hunter experience.