My Role
Work with VPs and directors and create concept mockups to align the CEO’s direction
Coordinate UX designers to facilitate the project discussion with PMs and technical leads
Collaborate with developers to deliver design details for implementation
Collaborate with UX researchers and data analysts for validation
Team
5 Directors
9 Product Managers
2 Program Managers
400+ Software Engineers
6 Frontend Engineers
5 Data Engineers
8 Data Analysts
6 UX Designers
4 Visual Designers
3 Technical Writers
2 UX Researchers
Background
Endpoint security solutions are served for corporate IT Administrators to deploy security agents in the company environment to monitor and remediate cyber threats. I started to contribute to the endpoint projects in December 2021.
By early 2023, the Trend Micro platform strategy had come to a mature place. Trend Micro has the unique strength of providing comprehensive protection among all security layers in the industry. Consolidating all solutions onto a single platform magnifies the threat prevention capability. The CEO, therefore, adjusted the endpoint security direction and expected to release the change at the following quarter's end.
Forming assumptions to decompose the mission
The key role to make the strategy transformation work is the user. Based on our customer engagement experience, the team formed 2 key assumptions to align with the CEO's direction.
1| IT admins need a single place for cyber security visibility and management, and endpoint solutions should be merged into Trend Vision One platform.
The focus of the cybersecurity industry has moved from single-security layer protection to cross-layer detection and response. Users must integrate the endpoint solution with their environment to have a more comprehensive and seamless security management experience.
2| IT admins have different security requirements for endpoints in different criticalities.
From the data of our existing endpoint products, customers protect critical servers with advanced security features which were not applied to all endpoints in the environment. Even if we provide a single platform for overall management, the design should allow users to manage the two types of endpoints differently simply.
The image concludes the key direction the project was aiming to.
Developing design strategy
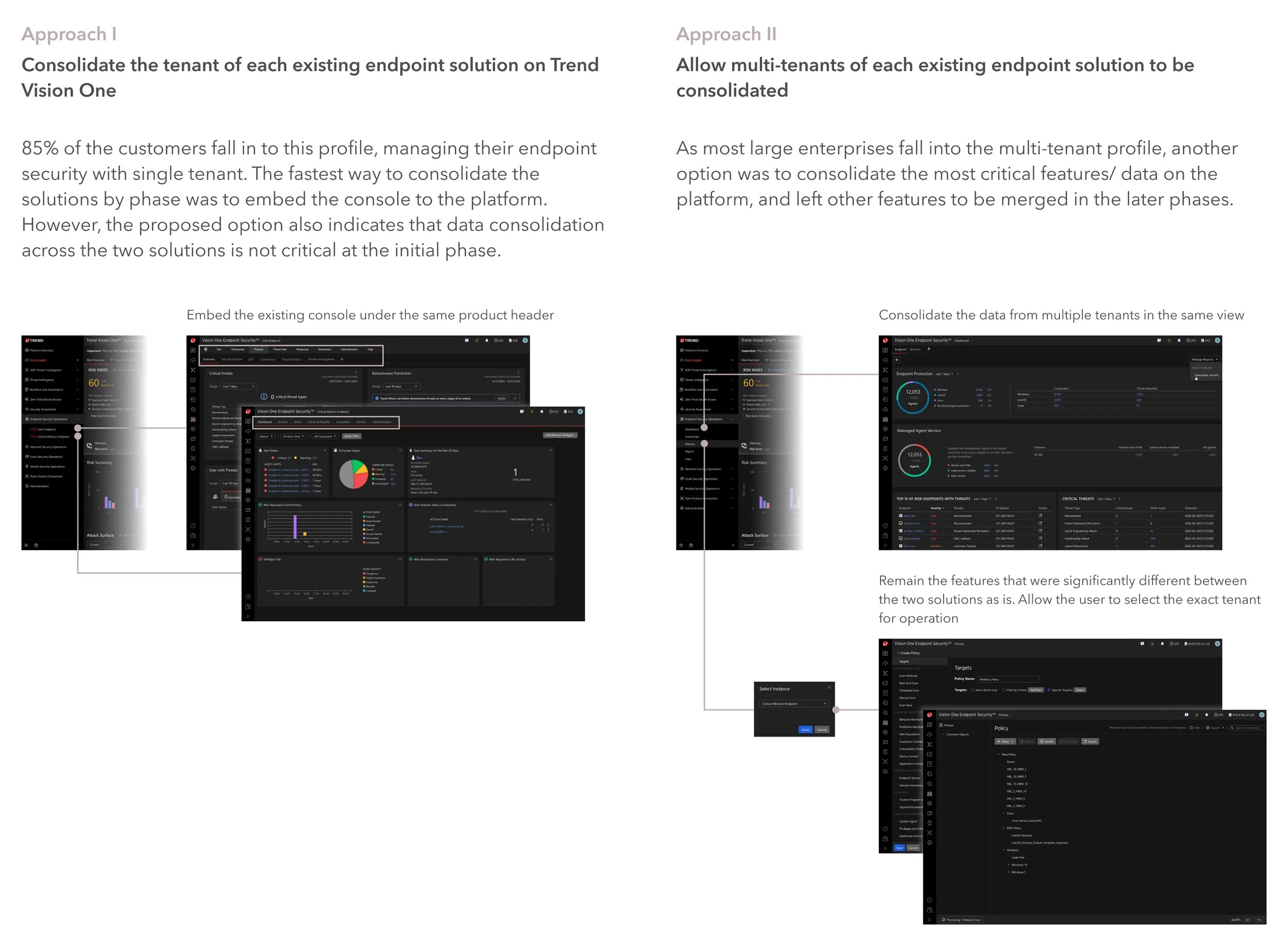
I participated in closed meetings with VPs and directors to understand the business goal and the impact according to the direction change. The initial and most critical debate was about the customer profile we aimed to serve. Corporations may manage their environments with multiple tenants in the SaaS world, but is it crucial to consolidate the data in the cybersecurity scenario? I proposed two potential solutions in different business approaches to facilitate the discussion.
After the business research and the internal validation, the team elaborated on Approach II since the type of profile is the major customer that brings the most value in meeting the company’s direction change. As the team reached the final consensus, I developed two design strategies for the upcoming design phase.
Planning, validation, and prioritisation
At this stage, we had to break down the high-level user flows, so that the team could estimate the effort and narrow the scope of the initial release as the implementation was expected to start in two weeks.
I coordinated five UX designers, three visual designers, and a technical writer to develop the end-to-end experience of the six customer types. The design team streamlined each customer type's use cases to onboard the new solution. The design communicated the direction change and aligned the language of communication to the leader group and was validated with executives, PMs, R&D engineer leaders, and data analysts. To prioritise, the team focused on two perspectives:
Whether the selective use cases in the MVP phase allow users at least self-serve to onboard
Whether the technical solutions were feasible
The discussion continued for two weeks, back and forth. The result was delivered to 400+ members, who helped to finalise the design and technical details and implement them in the following three months.
Example of the user flow of two of the customer types we validated with the team. The annotation in different colours noted down the discussed use case, technical decision, and design highlights we used for prioritisation.
The MVP design and iteration: take Agent Installer as an example
While prioritising the MVP scope, we identified that agent deployment is one of the most critical actions in an IT admin’s daily operation.
The goal was to instruct the user to deploy the right agent to the endpoint criticality level with the same experience. From the UX perspective, allowing users to choose with their needs is the most instinctive. However, with the cost and selling consideration, the marketing language, and the technical constraints, the team fell into debate.
As the selection result due to technical limitations might confuse the users, and the product marketing team confirmed to allow to exceed the purchased usage as promotion, after a few rounds of communication and iteration, we decided to guide the agent installer download by emphasising the feature difference.
Current results
Within a quarter, 30% of the upgraded customers have more than 2 of the existing endpoint products, which matches the assumption of requiring a consolidated management platform. Other upgraded customers have expanded the cybersecurity solution to other protection layers.
The net new customers do follow the instructions to select the exact agent for endpoint protection. However, the existing users stay with the original agent type they used, regardless of the UI instruction attempting to reeducate the user to distinguish the agents by feature.
Lessons learnt
The intensive schedule emphasised the importance of communication skills across roles. Each role needs different information for decision-making, knowing the audience and cutting to the chase boost efficiency.
On the other hand, despite the roles, it was also important to build a common language and align the consensus across the team. It took time to get the alignment, but reduced the cost of miscommunication. A massive team can be more efficient and productive than working as a small group.